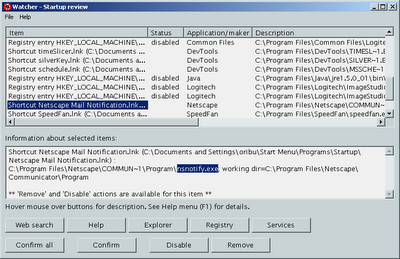
If you’re like me, you don’t like to install Anti-Virus software or any of the malware removing utilities on your system. The machine is sitting behind a firewall and I know what is running on the machine (most of the time).
That said, I’ve always wanted to have the equivalent of trip-wire or rkhunter from Linux/Unix land. An application that would monitor the rest of windows and would alert me when vital files/registry entries get touched. Well, I think I’ve found such beastie and it’s free to boot. Grab Tiny Watcher and install it on your windows box and let it run once to create a profile. From then on TW will monitor your system and tell you when some application/installer changes something vital on your machine. You also get the option to heal/remove/delete the changes after the fact.
Tiny Watcher checks the following point:
Processes
Registry keys or entries
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunServicesOnce (key)
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunServices (key)
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run (key)
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce (key)
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnceEx (key)
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunServicesOnce (key)
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunServices (key)
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run (key)
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce (key)
HKEY_CURRENT_USER\Software\Microsoft\WindowsNT\CurrentVersion\Windows\run (entry)
HKEY_CURRENT_USER\Software\Microsoft\WindowsNT\CurrentVersion\Windows\load (entry)
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run (key)
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run (key)
HKEY_LOCAL_MACHINE\Software\Microsoft\WindowsNT\CurrentVersion\Winlogon\Userinit (entry)
HKEY_LOCAL_MACHINE\Software\Microsoft\WindowsNT\CurrentVersion\Winlogon\Shell (entry)
HKEY_LOCAL_MACHINE\Software\Microsoft\WindowsNT\CurrentVersion\Winlogon\UIHost (entry)
HKEY_LOCAL_MACHINE\Software\Microsoft\WindowsNT\CurrentVersion\Winlogon\VmApplet (entry)
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Session Manager\BootExecute (entry)
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\ShellServiceObjectDelayLoad (key)
Services
All the subkeys of HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services are checked.
Other sensitive keys
HKEY_USERS\.Default\Software\Microsoft\Windows\CurrentVersion\Run (key)
HKEY_USERS\.Default\Software\Microsoft\Windows\CurrentVersion\RunOnce (key)
HKEY_LOCAL_MACHINE\Software\Microsoft\Active Setup\Installed Components (key)
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects (key)
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\WOW\cmdline (entry)
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\WOW\wowcmdline (entry)
HKEY_CLASSES_ROOT\vbsfile\shell\open\command\ (entry)
HKEY_CLASSES_ROOT\vbefile\shell\open\command\ (entry)
HKEY_CLASSES_ROOT\jsfile\shell\open\command\ (entry)
HKEY_CLASSES_ROOT\jsefile\shell\open\command\ (entry)
HKEY_CLASSES_ROOT\wshfile\shell\open\command\ (entry)
HKEY_CLASSES_ROOT\wsffile\shell\open\command\ (entry)
HKEY_CLASSES_ROOT\exefile\shell\open\command\ (entry)
HKEY_CLASSES_ROOT\comfile\shell\open\command\ (entry)
HKEY_CLASSES_ROOT\batfile\shell\open\command\ (entry)
HKEY_CLASSES_ROOT\scrfile\shell\open\command\ (entry)
HKEY_CLASSES_ROOT\piffile\shell\open\command\ (entry)
HKEY_CURRENT_USER\Control Panel\Desktop\SCRNSAVE.EXE (entry)
ini entries
win.ini, [windows], run
system.ini, [boot], shell
system.ini, [boot], scrnsave.exe
File scan
During a deep scan, a hashcode check (SHA-1) is made on the monitored files, therefore any change in a file’s content can be detected.
Note that a deep scan is automatically performed to create the snapshot (the first time Tiny Watcher runs). Content (files and subdirectories) of the following directories is checked:
NB: you can edit this list in the options window.
– C:\
– Windows directory (c:\Windows or c:\WinNT or other name, depending on your machine)
– Windows system32
– Windows system32\drivers
– Windows system
– Windows system\iosubsys
– Windows system\vmm32
Shortcut files (.lnk) in startup folders:
– For all users (e.g. “C:\Documents and Settings\All Users\Start Menu\Programs\Startup”, depending on your machine)
– For the current user (e.g. “C:\Documents and Settings\Owner\Start Menu\Programs\Startup”, depending on your machine)
The following separate files are also checked:
–
–
–
–
Scheduled tasks
Have Fun, and remember to stay safe :-)